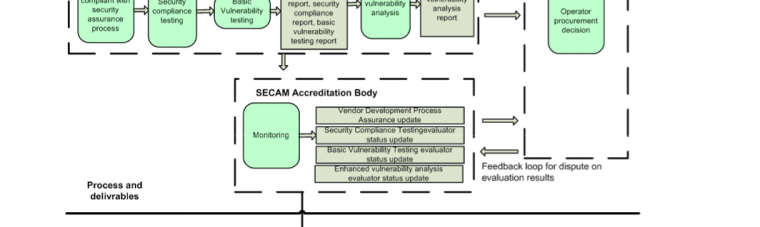
3GPP and GSMA to help vendors on improving equipment security
February 19, 2014 | Posted in News | By admin
Comments Off on 3GPP and GSMA to help vendors on improving equipment security
As Network Element security is often a very vulnerable Achilles’ heel of the telecom operator, either from the OAM network or from the signaling network (have a look on P1 Security’s Vulnerability Knowledge Base for details), it is a very
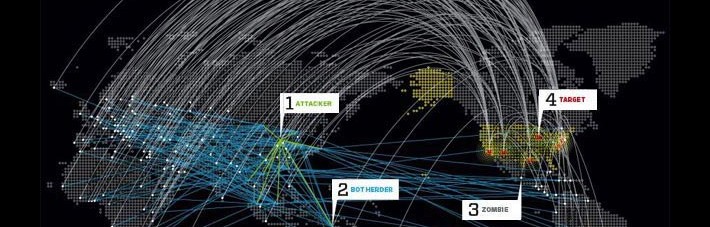
DoS auditing versus Fraudulent vendors of TDoS products/services with new multi-threaded SIP-based TDoS tool
November 15, 2013 | Posted in News | By admin
Comments Off on DoS auditing versus Fraudulent vendors of TDoS products/services with new multi-threaded SIP-based TDoS tool
TDoS is a rising concern for operators of both traditional and VoIP networks: extortion, subscriber targeting denial of service attacks, … There are many reasons and unprotected infrastructures that combine to create downtime in telecom service. TDoS & DDoS testing
Cisco Security Advisory: Cisco IOS Software Session Initiation Protocol Denial of Service Vulnerability

November 6, 2013 | Posted in Advisories | By admin
Comments Off on Cisco Security Advisory: Cisco IOS Software Session Initiation Protocol Denial of Service Vulnerability
Vulnerability in Cisco VoIP protocol SIP can cause temporary Denial of Service. Cisco Security Advisory: Cisco IOS Software Session Initiation Protocol Denial of Service Vulnerability.
SIM Cards attacks using Over-the-Air Updates

July 22, 2013 | Posted in News | By admin
Comments Off on SIM Cards attacks using Over-the-Air Updates
The attack is a combination of both insecure communication method of SIM cards update with OTA STK procedure; and vulnerability in Java version running on the SIM card. Industry reality is: Number of affected card is not very high, limited
NSA eavesdropping of undersea telecom cables

July 10, 2013 | Posted in News | By admin
Comments Off on NSA eavesdropping of undersea telecom cables
As many Snowden-revealed NSA document show, NSA is actively involved with breaking in and tapping undersea cables including high-speed telecom and internet optical fibers. These surveillance, tapping and sniffing may have been enabled both by hacking and by physical submarine operation