Washington Post: How the NSA infers relationships based on mobile location data from SS7 and GRX
May 4, 2014 | Posted in News | By admin
Comments Off on Washington Post: How the NSA infers relationships based on mobile location data from SS7 and GRX
A new article shows preoccupying combination of SS7 and GRX interception, OTT app HTTP calls eavedropping and datawarehousing to extract subscriber privacy details from Telecom and Mobile operators.
Washington Post: New documents show how the NSA infers relationships based on mobile location data.
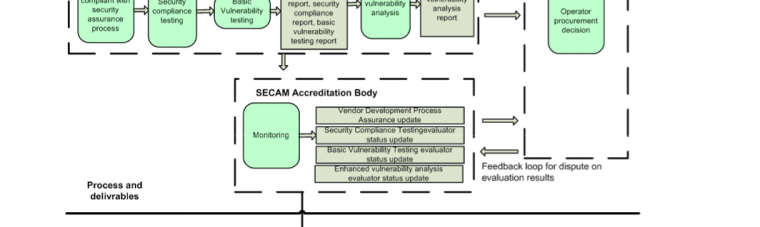
3GPP and GSMA to help vendors on improving equipment security
February 19, 2014 | Posted in News | By admin
Comments Off on 3GPP and GSMA to help vendors on improving equipment security
As Network Element security is often a very vulnerable Achilles’ heel of the telecom operator, either from the OAM network or from the signaling network (have a look on P1 Security’s Vulnerability Knowledge Base for details), it is a very good thing that 3GPP SECAM and GSMA NESAG / NESEC groups are coming to release.
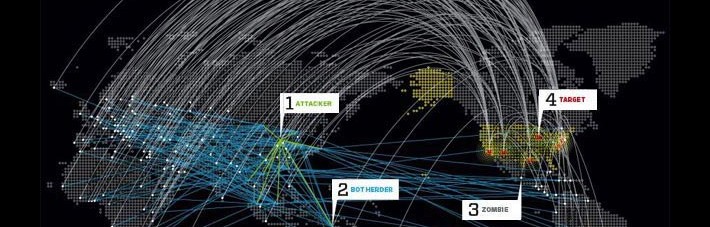
DoS auditing versus Fraudulent vendors of TDoS products/services with new multi-threaded SIP-based TDoS tool
November 15, 2013 | Posted in News | By admin
Comments Off on DoS auditing versus Fraudulent vendors of TDoS products/services with new multi-threaded SIP-based TDoS tool
TDoS is a rising concern for operators of both traditional and VoIP networks: extortion, subscriber targeting denial of service attacks, … There are many reasons and unprotected infrastructures that combine to create downtime in telecom service.
TDoS & DDoS testing | P1 Security.
Cisco Security Advisory: Cisco IOS Software Session Initiation Protocol Denial of Service Vulnerability

November 6, 2013 | Posted in Advisories | By admin
Comments Off on Cisco Security Advisory: Cisco IOS Software Session Initiation Protocol Denial of Service Vulnerability
Vulnerability in Cisco VoIP protocol SIP can cause temporary Denial of Service.
Belgacom hacks and spying show the needs to strongly improve telecom security

October 25, 2013 | Posted in News | By admin
Comments Off on Belgacom hacks and spying show the needs to strongly improve telecom security
“Several of us around the table had been subject to surveillance,” he told reporters.”The least we can expect is the countries and security services involve change their practices.”
“According to De Standaard, […] the spying was carried out by the U.S. National Security Agency and involved tracking international telephone calls for two years. It was focused on BICS, the Belgacom unit which provides wholesale telecom infrastructure services–in particular in Africa and the Middle East.”
Belgacom claims it was spied on by NSA.
Belgium latest to seek answers on spying allegations.
France in the NSA’s crosshair : phone networks under surveillance
October 21, 2013 | Posted in News | By admin
Comments Off on France in the NSA’s crosshair : phone networks under surveillance
Le Monde article on NSA spying on France telecom networks based on Snowden leaks.
“According to the documents retrieved from the NSA database […] telephone communications of French citizens are intercepted on a massive scale.”
“The techniques used for these interceptions appear under the codenames ‘DRTBOX’ and ‘WHITEBOX’. Their characteristics are not known either. But we do know that, thanks to DRTBOX, 62.5 million data were collected in France and that WHITEBOX enables the recording of 7.8 million elements. ”
New report: Is Huawei in Ericsson’s shoes when Athens Affair hit?

October 18, 2013 | Posted in News | By admin
Comments Off on New report: Is Huawei in Ericsson’s shoes when Athens Affair hit?
Huawei is trying to clear its name from the allegations of spying. But is Huawei really worse and compromised than Ericsson.
Ericsson backdoored products were used by intelligence agencies to spy on Greek government officials and hundred of VIP mobile phones, yet Ericsson did not suffer from the same level of ban and bad press that Huawei did get.
Is it a cultural bias against Huawei? A political and economical against chinese manufacturer? Or the level of compromission of Huawei is much higher, prompting this reaction.
Huawei is nevertheless trying to clear its name from these allegations with the following report “Cyber Security Perspectives” by John Suffolk, Huawei SVP & Global Cyber Security Officer.
PDF Report: Huawei Cyber Security White Paper (Oct. 2013)
Huawei: We are not spying on you.
SIM Cards attacks using Over-the-Air Updates

July 22, 2013 | Posted in News | By admin
Comments Off on SIM Cards attacks using Over-the-Air Updates
The attack is a combination of both insecure communication method of SIM cards update with OTA STK procedure; and vulnerability in Java version running on the SIM card.
Industry reality is:
- Number of affected card is not very high, limited to old cards. Often it’s 3DES being used.
- The Binary SMS required to deliver the attack are often filtered at operator’s boundary, thus stopping the attack.
Hijacking SIM Cards through Over-the-Air Updates | Symantec Connect Community.
DES encryption leaves SIM cards vulnerable to exploitation | ZDNet.
News and Threat Research Millions of SIM cards vulnerable to remote compromise | Fortinet Blog.
NSA eavesdropping of undersea telecom cables

July 10, 2013 | Posted in News | By admin
Comments Off on NSA eavesdropping of undersea telecom cables
As many Snowden-revealed NSA document show, NSA is actively involved with breaking in and tapping undersea cables including high-speed telecom and internet optical fibers. These surveillance, tapping and sniffing may have been enabled both by hacking and by physical submarine operation with secret cover stories even within US DoD.
NSA slide shows surveillance of undersea cables – The Washington Post.
A connected world – The Washington Post.
Undersea Optical Cable Cuts – Cypherpunks.
The Creepy, Long-Standing Practice of Undersea Cable Tapping – Olga Khazan – The Atlantic.
NSA Spying on Europe/Asia SEA-ME-WE-4 Undersea Telecom Cables | LeakSource.
French telecom operator Orange threatens to sue NSA over cable tapping — RT News.
Operation Tempora: GCHQ taps fibre-optic cables for secret access to world’s communications | UK news | The Guardian

June 21, 2013 | Posted in News | By admin
Comments Off on Operation Tempora: GCHQ taps fibre-optic cables for secret access to world’s communications | UK news | The Guardian
Operation Tempora: GCHQ taps fibre-optic cables for secret access to world’s communications.
“Britain’s spy agency GCHQ has secretly gained access to the network of cables which carry the world’s phone calls and internet traffic”.
“The sheer scale of the agency’s ambition is reflected in the titles of its two principal components: Mastering the Internet and Global Telecoms Exploitation, aimed at scooping up as much online and telephone traffic as possible. ”
“GCHQ was handling 600m “telephone events” each day, had tapped more than 200 fibre-optic cables and was able to process data from at least 46 of them at a time.”
GCHQ taps fibre-optic cables for secret access to world’s communications | UK news | The Guardian.
